Ahhh oki if its a false thing by Bitdefender, Im fine with stopping, Thank you soo much for helping me try and remove it. If it won’t effect my pc then I’m fine with keeping it there since its a false positive.
Trying to remove Generic.Trojan.DiscordStealer.B.D6426E8C
Collapse
X
-
-
I would like you to run the last fix for FRST and post the log, and out of curiosity run rogue killer, then we can clean up the tools we used and send you on your way. Maybe even zip up and upload the entire .xml file if you could, so I can submit it to Bitdefender.Comment
-
-
-
-
-
As part of the process I sent a couple files to Virustotal This one came back with 4 hits, are you sure this file is safe?
[COLOR=rgb(184, 49, 47)]C:\ProgramData\Nexon\NGS\NGService.exe VirusTotal
This one came back with one hit.[COLOR=rgb(184, 49, 47)] D:\Steam\steamapps\common\wallpaper_engine\bin\wal lpaperservice32_c.exe => VirusTotal
Also, one file was not able to be removed.
AlternateDataStreams: C:\Users\theph\AppData\Local\Temp:$DATA [16]
C:\Users\theph\AppData\Local\Temp => [COLOR=rgb(184, 49, 47)]“:$DATA” ADS could not remove.
We do need to address these issues before I send you on the way. I will create a new fixlist based on your response. I personally think this file needs to go. No .exe file should be running from the program data folder to be honest.[/COLOR][/COLOR][/COLOR]Comment
-
The 2nd one is from Steam and its a wallpaper engine from there, I doubt steam would let a trojan in on there program.Comment
-
Ok, lets remove the other one. I will leave the steam. I need you to run this fix for me in safe mode, after the rogue killer scan. Maybe this is what bitdefender is detecting. We will see…
Copy the content of the code box below.
Do not copy the word code!!!
Right Click FRST and run as Administrator.
Click Fix once (!) and wait. The program will create a log file (Fixlog.txt).
Attach it to your next message.
[COLOR=rgb(184, 49, 47)]Edit: Seems the legit file should be displayed the same as below in a FRST log. I believe we may have found the culprit, these guys are getting crafty at hiding things and making them seem legit.Code:Start:: CloseProcesses: SystemRestore: On CreateRestorePoint: DeleteKey: HKU\.DEFAULT\SOFTWARE\Nexon C:\ProgramData\Nexon\NGS\NGService.exe C:\ProgramData\Nexon\NGS C:\ProgramData\Nexon AlternateDataStreams: C:\Users\theph\AppData\Local\Temp:$DATA [16] CMD: del /f /s /q %windir%\prefetch\*.* CMD: del /s /q "%userprofile%\AppData\Local\temp\*.*" CMD: ipconfig /flushdns C:\Windows\Temp\*.* C:\WINDOWS\system32\*.tmp C:\WINDOWS\syswow64\*.tmp emptytemp: Reboot: End::
S3 NGS; C:\WINDOWS\NGService.exe [3134240 2022-07-17] (NEXON Korea Corporation. → NEXON Korea Corporation)[/COLOR]Comment
-
It says Everything is good so far NO Detection
Code:Program : RogueKiller Anti-Malware Version : 15.6.4.0 x64 : Yes Program Date : Dec 15 2022 Location : C:\Program Files\RogueKiller\RogueKiller64.exe Premium : No Company : Adlice Software Website : https://www.adlice.com/ Contact : Support Form | Contact • Adlice Software Website : Free Virus Cleaner | RogueKiller AntiMalware • Adlice Software Operating System : Windows 10 (10.0.19044) 64-bit 64-bit OS : Yes Startup : 0 WindowsPE : No User : ThePhoenixVR User is Admin : Yes Date : 2023/01/02 15:43:36 Type : Scan Aborted : No Scan Mode : Standard Duration : 1111 Found items : 0 Total scanned : 186508 Signatures Version : 20210423_062556 Truesight Driver : Yes Updates Count : 8 ************************* Warnings ************************* ************************* Updates ************************* Git (64-bit), version 2.37.3 [+] Available Version : 2.39.0 [+] Size : 266 MB [+] Wow6432 : No [+] Portable : No [+] update_location : D:\Waifu thing\Git\ WinRAR 6.02 (64-bit) (64-bit), version 6.02.0 [+] Available Version : 6.11 [+] Wow6432 : No [+] Portable : No [+] update_location : C:\Program Files\WinRAR\ Java 8 Update 321 (64-bit) (64-bit), version 8.0.3210.7 [+] Available Version : 8.0.3330.0 [+] Size : 49.1 MB [+] Wow6432 : No [+] Portable : No [+] update_location : C:\Program Files\Java\jre1.8.0_321\ paint.net (64-bit), version 4.3.11 [+] Available Version : 4.3.12 [+] Size : 220 MB [+] Wow6432 : No [+] Portable : No Notepad++ (32-bit x86) (32-bit), version 8.4.4 [+] Available Version : 8.4.8 [+] Size : 12.6 MB [+] Wow6432 : Yes [+] Portable : No OBS Studio (32-bit), version 27.1.3 [+] Available Version : 28.1.2 [+] Wow6432 : Yes [+] Portable : No Discord (64-bit), version 1.0.9007 [+] Available Version : 1.0.9008 [+] Size : 78.4 MB [+] Wow6432 : No [+] Portable : No [+] update_location : C:\Users\theph\AppData\Local\Discord Python 3.10.6 (64-bit) (64-bit), version 3.10.6150.0 [+] Available Version : 3.11.1000.0 [+] Size : 105 MB [+] Wow6432 : No [+] Portable : No ************************* Processes ************************* ************************* Modules ************************* ************************* Services ************************* ************************* Scheduled Tasks ************************* ************************* Registry ************************* ************************* WMI ************************* ************************* Hosts File ************************* is_too_big : No hosts_file_path : C:\Windows\System32\drivers\etc\hosts ************************* Filesystem ************************* ************************* Web Browsers ************************* ************************* Antirootkit *************************
Comment
-
-
[COLOR=rgb(184, 49, 47)]Originally posted by MalnutritionOk, lets remove the other one. I will leave the steam. I need you to run this fix for me in safe mode, after the rogue killer scan. Maybe this is what bitdefender is detecting. We will see…
Copy the content of the code box below.
Do not copy the word code!!!
Right Click FRST and run as Administrator.
Click Fix once (!) and wait. The program will create a log file (Fixlog.txt).
Attach it to your next message.
[COLOR=rgb(184, 49, 47)]Edit: Seems the legit file should be displayed the same as below in a FRST log. I believe we may have found the culprit, these guys are getting crafty at hiding things and making them seem legit.Code:Start:: CloseProcesses: SystemRestore: On CreateRestorePoint: DeleteKey: HKU\.DEFAULT\SOFTWARE\Nexon C:\ProgramData\Nexon\NGS\NGService.exe C:\ProgramData\Nexon\NGS C:\ProgramData\Nexon AlternateDataStreams: C:\Users\theph\AppData\Local\Temp:$DATA [16] CMD: del /f /s /q %windir%\prefetch\*.* CMD: del /s /q "%userprofile%\AppData\Local\temp\*.*" CMD: ipconfig /flushdns C:\Windows\Temp\*.* C:\WINDOWS\system32\*.tmp C:\WINDOWS\syswow64\*.tmp emptytemp: Reboot: End::
S3 NGS; C:\WINDOWS\NGService.exe [3134240 2022-07-17] (NEXON Korea Corporation. → NEXON Korea Corporation)
[/COLOR]
Ohhhh so it could be NEXON doing it
Im trying to put my computer in safe mode but its not letting me do it, It stays black for awhile and then turns off, I turn it back on and its not in safe mode.[/color]Comment
-
Ok, run the fix in normal mode. Let’s see how it goes. If further action needs to be taken on the file that would not delete we will do so if needed.
I think it’s a possibility that you have a fake version of the Nexon. If you will notice from my edit. The legit file loads from C:\Windows, the file you have is loading from program data folder. Also, now looking at your installed programs, Nexon is not listed, so indeed this may be the culprit.Originally posted by Phoenix VROhhhh so it could be NEXON doing it
Run the fix in normal mode, then post the log created please.Comment
-
-
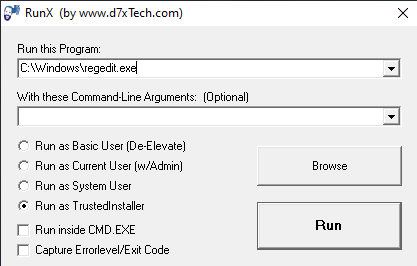
Ok, one last fix, then I want you to scan again with Bitdefender after this.
First download RunX
 Current version: 1.0.0.1 Released May 19th, 2021 (fixed a bug with launching processes in general d7x code as explained here.) RunX is designed to easily launch any process with System account or…
Current version: 1.0.0.1 Released May 19th, 2021 (fixed a bug with launching processes in general d7x code as explained here.) RunX is designed to easily launch any process with System account or…
Unzip it to your desktop.
Where FRST and RunX.exe are side by side.
[ATTACH type=“full” alt=“1672677976949.png”]11225[/ATTACH]
Then drag FRST onto RunX.
Make sure [COLOR=rgb(184, 49, 47)]run as trusted installer it ticked.
Then click the Run button.
[ATTACH type=“full” alt=“1672678127383.png”]11226[/ATTACH]
This will start FRST with Trusted Installer Permissiion, and will be able to delete this C:\Users\theph\AppData\Local\Temp:$DATA [16] which is being stubborn. Then you just run the fix as normal after FRST is started thru RunX
Copy the content of the code box below.
[COLOR=rgb(184, 49, 47)]Do not copy the word code!!!
Right Click FRST and run as Administrator.
Click Fix once (!) and wait. The program will create a log file (Fixlog.txt).
Attach it to your next message.
[/COLOR][/COLOR]Code:Start:: CloseProcesses: SystemRestore: On CreateRestorePoint: AlternateDataStreams: C:\Users\theph\AppData\Local\Temp:$DATA [16] CMD: del /s /q "%userprofile%\AppData\Local\temp\*.*" C:\Windows\Temp\*.* C:\WINDOWS\system32\*.tmp C:\WINDOWS\syswow64\*.tmp emptytemp: Reboot: End::
Comment
Comment