-
Hi there and welcome to PC Help Forum (PCHF), a more effective way to get the Tech Support you need!
We have Experts in all areas of Tech, including Malware Removal, Crash Fixing and BSOD's , Microsoft Windows, Computer DIY and PC Hardware, Networking, Gaming, Tablets and iPads, General and Specific Software Support and so much more.
Why not Click Here To Sign Up and start enjoying great FREE Tech Support.
This site uses cookies. By continuing to use this site, you are agreeing to our use of cookies. Learn More.
Solved I think I am infected and want to check
- Thread starter Cory
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.

- Status
- Not open for further replies.
Stupid question but was this the .com at one time?
Different site.
I see no real indicator of malware on your machine, what issues are you having that brings you here?
VirusTotal Scan.
- Please go to VirusTotal.
- Click the Choose File button.
- Navigate to >>>>>>>> C:\Windows\system32\{A6D608F0-0BDE-491A-97AE-5C4B05D86E01}.bat
- or simply copy and paste it.
- Click the Scan it! button.
- You might see a message saying File already analysed, if you do click Reanalyse.
- Wait for all the scans to finish then copy and paste the web address from your broswer's address bar.
Example of web address :
- Include the link in your next reply.
Download attached fixlist.txt file and save it to the Desktop. NOTE. It's important that both files, FRST/FRST64 and fixlist.txt are in the same location or the fix will not work. NOTICE: This script was written specifically for this user, for use on that particular machine. Running this on another machine may cause damage to your operating system Run FRST/FRST64 and press the Fix button just once and wait. If for some reason the tool needs a restart, please make sure you let the system restart normally. After that let the tool complete its run. When finished FRST will generate a log on the Desktop (Fixlog.txt). Please post it to your reply.
Clean up temp files and reduce startup load with CCleaner.
Note: This tool will clean your browsing history as well.
- Download CCleaner from here.
- After install Click Options.
- Go to monitoring.
- Uncheck All Monitoring items.
- Go to advanced -- Click close program after cleaning.
- Go to settings -- click run ccleaner when the computer starts.
- Now that you have ccleaner installed and set-up:
- Open the program.
- Go to Tools
- Go to Startup
- Now double click each item. To Disable.
- Leave only your antivirus enabled.
- Then disable All items in your scheduled task as well.
- Unless they are related to windows defender.Or your antivirus.
- Reboot the machine.
Please download Zhp Cleaner to your desktop. Right Click the icon and select run as administrator.
2. Once you have started the program, you will need to click the scanner button.

The program will close all open browsers!
3. Once the scan is completed, the you will want to click the Repair button.
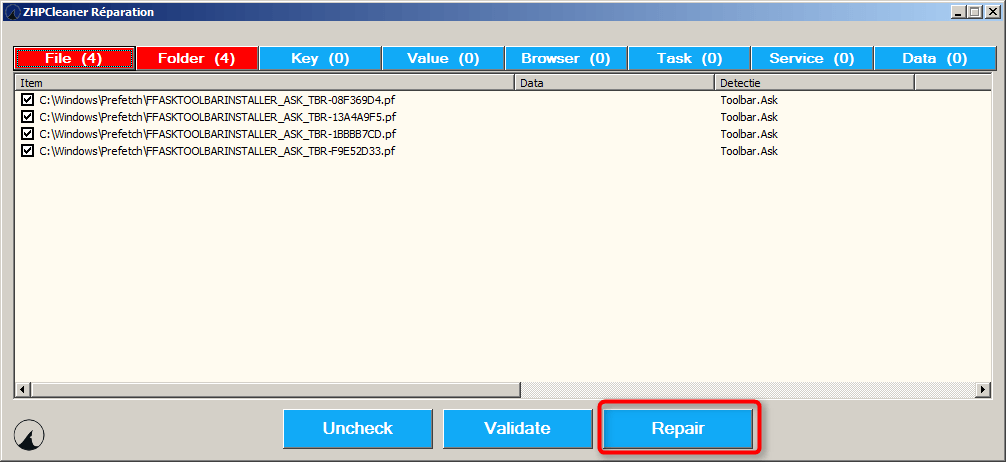
At the end of the process you may be asked to reboot your machine. After you reboot a report will open on your desktop.
Copy and paste the report here in your next reply.
Attachments
Thanks, for the quick reply. I tried running the aswmbr but got the blue screen. My son was downloading a texture pack for minecraft and one of the fake security screens popped up looking official and from Microsoft.
I will start on the rest of the work that you added.
I will start on the rest of the work that you added.
I do not find "C:\Windows\system32\{A6D608F0-0BDE-491A-97AE-5C4B05D86E01}.bat" in the first step.
Well, it is not a windows file and it appears suspicious... We will remove it in a bit, after all of the above please do the following.
Rogue Killer Scan.
Download RogueKiller from one of the following links and save it to your Desktop:
Link 1
Link 2
- Close all the running programs
- Double click on downloaded setup.exe file to install the program.
- Click on Start Scan button.
- Click on another Start Scan button.
- Wait until the Status box shows Scan Finished
- Click on Delete.
- Wait until the Status box shows Deleting Finished.
- Click on Report and copy/paste the content of the Notepad into your next reply.
- RKreport.txt could also be found on your desktop.
- If more than one log is produced post all logs.
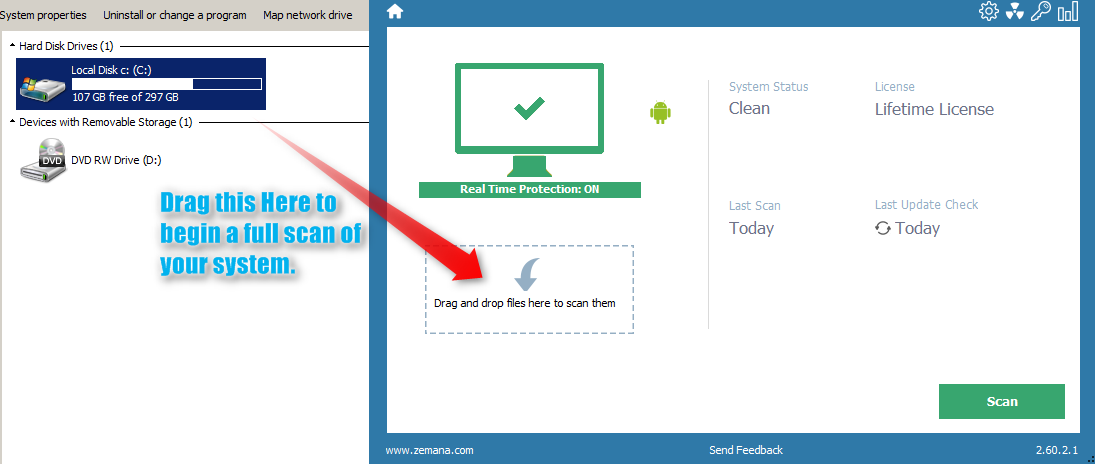
Zemana Deep Scan.
- Right click on Zemana and run as admin.
- Click the Cog/Sproket Wheel, at the top right of Zemana
- Select Advanced - I have read the warning and wish to proceed.
- Place a tick next to Detect Suspicious (Root CA) Certificates.
- Then click the house icon in Zemana.
- Then hit your start button at the lower left hand corner of your desktop.
- Then left click on Computer.
- Drag Local Disk C: Into the area of Zemana that reads Drag and drop files here to scan them.
- Once the scan has completed click graph icon on the top right of the programs User interface.
- Double click to open the latest log-file.
- Copy it to your clipboard.
- Post the log here in your next reply.
Here is the rogueKiller report:
RogueKiller V12.9.7.0 (x64) [Feb 6 2017] (Free) by Adlice Software
mail : http://www.adlice.com/contact/
Feedback : http://forum.adlice.com
Website : http://www.adlice.com/download/roguekiller/
Blog : http://www.adlice.com
Operating System : Windows 10 (10.0.10586) 64 bits version
Started in : Normal mode
User : CRJ [Administrator]
Started from : C:\Users\CRJ\Desktop\RogueKillerX64.exe
Mode : Delete -- Date : 02/17/2017 06:40:14 (Duration : 00:18:41)
¤¤¤ Processes : 0 ¤¤¤
¤¤¤ Registry : 2 ¤¤¤
[Suspicious.Path] (X64) HKEY_LOCAL_MACHINE\System\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\FirewallRules | {8A929421-DBC9-43A3-B823-7701E1831825} : v2.25|Action=Allow|Active=TRUE|Dir=In|Protocol=6|Profile=Private|App=C:\Users\CRJ\AppData\Local\Temp\WZSE0.TMP\Common\EpsonNet Setup\ENEasyApp.exe|Name=EpsonNet Setup| [x] -> Not selected
[Suspicious.Path] (X64) HKEY_LOCAL_MACHINE\System\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\FirewallRules | {8E183632-AE0D-4A77-80F5-721A212C4BD8} : v2.25|Action=Allow|Active=TRUE|Dir=In|Protocol=17|Profile=Private|App=C:\Users\CRJ\AppData\Local\Temp\WZSE0.TMP\Common\EpsonNet Setup\ENEasyApp.exe|Name=EpsonNet Setup| [x] -> Not selected
¤¤¤ Tasks : 0 ¤¤¤
¤¤¤ Files : 2 ¤¤¤
[Adw.DNSUnlocker][File] C:\Program Files (x86)\Steam\depotcache\223851_1463440244266315419.manifest -> Deleted
[Adw.DNSUnlocker][File] C:\Program Files (x86)\Steam\depotcache\223851_5648498717833789511.manifest -> Deleted
¤¤¤ WMI : 0 ¤¤¤
¤¤¤ Hosts File : 0 ¤¤¤
¤¤¤ Antirootkit : 0 (Driver: Loaded) ¤¤¤
¤¤¤ Web browsers : 1 ¤¤¤
[PUM.HomePage][Chrome:Config] Default [SecurePrefs] : homepage [http://mysyngenta.intra/] -> Not selected
¤¤¤ MBR Check : ¤¤¤
+++++ PhysicalDrive0: NVMe Samsung SSD 950 +++++
--- User ---
[MBR] bddb33cc9fe54b4a40aa0ed568199f59
[BSP] 242e9a4212b4bd7ce1156d07b361f117 : Windows Vista/7/8|VT.Unknown MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x7) [VISIBLE] Offset (sectors): 2048 | Size: 500 MB [Windows Vista/7/8 Bootstrap | Windows Vista/7/8 Bootloader]
1 - [XXXXXX] NTFS (0x7) [VISIBLE] Offset (sectors): 1026048 | Size: 487884 MB [Windows Vista/7/8 Bootstrap | Windows Vista/7/8 Bootloader]
User = LL1 ... OK
Error reading LL2 MBR! ([1] Incorrect function. )
RogueKiller V12.9.7.0 (x64) [Feb 6 2017] (Free) by Adlice Software
mail : http://www.adlice.com/contact/
Feedback : http://forum.adlice.com
Website : http://www.adlice.com/download/roguekiller/
Blog : http://www.adlice.com
Operating System : Windows 10 (10.0.10586) 64 bits version
Started in : Normal mode
User : CRJ [Administrator]
Started from : C:\Users\CRJ\Desktop\RogueKillerX64.exe
Mode : Delete -- Date : 02/17/2017 06:40:14 (Duration : 00:18:41)
¤¤¤ Processes : 0 ¤¤¤
¤¤¤ Registry : 2 ¤¤¤
[Suspicious.Path] (X64) HKEY_LOCAL_MACHINE\System\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\FirewallRules | {8A929421-DBC9-43A3-B823-7701E1831825} : v2.25|Action=Allow|Active=TRUE|Dir=In|Protocol=6|Profile=Private|App=C:\Users\CRJ\AppData\Local\Temp\WZSE0.TMP\Common\EpsonNet Setup\ENEasyApp.exe|Name=EpsonNet Setup| [x] -> Not selected
[Suspicious.Path] (X64) HKEY_LOCAL_MACHINE\System\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\FirewallRules | {8E183632-AE0D-4A77-80F5-721A212C4BD8} : v2.25|Action=Allow|Active=TRUE|Dir=In|Protocol=17|Profile=Private|App=C:\Users\CRJ\AppData\Local\Temp\WZSE0.TMP\Common\EpsonNet Setup\ENEasyApp.exe|Name=EpsonNet Setup| [x] -> Not selected
¤¤¤ Tasks : 0 ¤¤¤
¤¤¤ Files : 2 ¤¤¤
[Adw.DNSUnlocker][File] C:\Program Files (x86)\Steam\depotcache\223851_1463440244266315419.manifest -> Deleted
[Adw.DNSUnlocker][File] C:\Program Files (x86)\Steam\depotcache\223851_5648498717833789511.manifest -> Deleted
¤¤¤ WMI : 0 ¤¤¤
¤¤¤ Hosts File : 0 ¤¤¤
¤¤¤ Antirootkit : 0 (Driver: Loaded) ¤¤¤
¤¤¤ Web browsers : 1 ¤¤¤
[PUM.HomePage][Chrome:Config] Default [SecurePrefs] : homepage [http://mysyngenta.intra/] -> Not selected
¤¤¤ MBR Check : ¤¤¤
+++++ PhysicalDrive0: NVMe Samsung SSD 950 +++++
--- User ---
[MBR] bddb33cc9fe54b4a40aa0ed568199f59
[BSP] 242e9a4212b4bd7ce1156d07b361f117 : Windows Vista/7/8|VT.Unknown MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x7) [VISIBLE] Offset (sectors): 2048 | Size: 500 MB [Windows Vista/7/8 Bootstrap | Windows Vista/7/8 Bootloader]
1 - [XXXXXX] NTFS (0x7) [VISIBLE] Offset (sectors): 1026048 | Size: 487884 MB [Windows Vista/7/8 Bootstrap | Windows Vista/7/8 Bootloader]
User = LL1 ... OK
Error reading LL2 MBR! ([1] Incorrect function. )
Attachments
Here is the Zemana log:
Zemana AntiMalware 2.72.2.101 (Installed)
-------------------------------------------------------
Scan Result : Completed
Scan Date : 2017/2/17
Operating System : Windows 10 64-bit
Processor : 4X Intel(R) Core(TM) i5-6600K CPU @ 3.50GHz
BIOS Mode : Legacy
CUID : 1437DDB1AFEE1141DF3D03
Scan Type : Custom Scan
Duration : 8m 56s
Scanned Objects : 367296
Detected Objects : 0
Excluded Objects : 0
Read Level : SCSI
Auto Upload : Enabled
Detect All Extensions : Disabled
Scan Documents : Disabled
Domain Info : WORKGROUP,0,2
Detected Objects
-------------------------------------------------------
No threats detected
Zemana AntiMalware 2.72.2.101 (Installed)
-------------------------------------------------------
Scan Result : Completed
Scan Date : 2017/2/17
Operating System : Windows 10 64-bit
Processor : 4X Intel(R) Core(TM) i5-6600K CPU @ 3.50GHz
BIOS Mode : Legacy
CUID : 1437DDB1AFEE1141DF3D03
Scan Type : Custom Scan
Duration : 8m 56s
Scanned Objects : 367296
Detected Objects : 0
Excluded Objects : 0
Read Level : SCSI
Auto Upload : Enabled
Detect All Extensions : Disabled
Scan Documents : Disabled
Domain Info : WORKGROUP,0,2
Detected Objects
-------------------------------------------------------
No threats detected
What Rogue killer found is likely a false positive. Your machine is clean, it was likely just a pop up from a bad website, should be nothing to worry about unless it is happening constantly across many websites.
Just go ahead and post the FRST fix and the ZHP scan, and let me know if there are any other issues.
Just go ahead and post the FRST fix and the ZHP scan, and let me know if there are any other issues.
Here is the final scans. It took me a while to figure out the fix file for FRST. Had to change the file name to the correct one. lol. Thanks I appreciate everything.
Recommendations on what to maintain going forward would be great.
Recommendations on what to maintain going forward would be great.
Fix result of Farbar Recovery Scan Tool (x64) Version: 18-02-2017
Ran by CRJ (18-02-2017 09:23:20) Run:1
Running from C:\Users\CRJ\Desktop
Loaded Profiles: CRJ (Available Profiles: CRJ & Connor)
Boot Mode: Normal
==============================================
fixlist content:
*****************
Start
CreateRestorePoint:
Closeprocesses:
Emptytemp:
HKU\S-1-5-21-517047234-2264697268-270894284-1001\...\Run: [BingSvc] => C:\Users\CRJ\AppData\Local\Microsoft\BingSvc\BingSvc.exe [144008 2015-11-05] (© 2015 Microsoft Corporation)
HKU\S-1-5-21-517047234-2264697268-270894284-1001\...\MountPoints2: {186b6caa-c16c-11e5-b600-806e6f6e6963} - "D:\Run.exe"
Tcpip\Parameters: [DhcpNameServer] 75.75.76.76 75.75.75.75
Tcpip\..\Interfaces\{ee5e4c75-c85d-40a3-bd68-be942d47caa5}: [DhcpNameServer] 75.75.76.76 75.75.75.75
Tcpip\..\Interfaces\{f7f70cc0-e9e3-4107-af44-16e61c7af5d0}: [DhcpNameServer] 75.75.76.76 75.75.75.75
CHR HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Google\Chrome\Extensions\...\Chrome\Extension: [fcfenmboojpjinhpgggodefccipikbpd] - hxxps://clients2.google.com/service/update2/crx
CHR HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Google\Chrome\Extensions\...\Chrome\Extension: [lmjegmlicamnimmfhcmpkclmigmmcbeh] - hxxps://clients2.google.com/service/update2/crx
Task: {30F7F9CC-172A-4F36-A08C-13D4D7755C15} - System32\Tasks\GoogleUpdateTaskMachineCore => C:\Program Files (x86)\Google\Update\GoogleUpdate.exe [2016-01-23] (Google Inc.)
Task: {B51668C0-CB6F-4E85-9B47-3625060731EC} - System32\Tasks\EPSON WF-2660 Series Update {7A42C501-E959-4055-A7F6-78911F11D381} => C:\Windows\system32\spool\DRIVERS\x64\3\E_YTSMAE.EXE [2013-11-22] (SEIKO EPSON CORPORATION)
Task: {B6377F1B-92D9-4EAB-BF75-2A9E7F147880} - System32\Tasks\GoogleUpdateTaskMachineUA => C:\Program Files (x86)\Google\Update\GoogleUpdate.exe [2016-01-23] (Google Inc.)
Task: {D8F55054-7AEF-4343-8B4B-8863A85C9B15} - System32\Tasks\Microsoft\Windows\RemovalTools\MRT_HB => C:\Windows\system32\MRT.exe [2017-01-11] (Microsoft Corporation)
Task: {F0F421B5-4194-4B5E-9637-35C30E22FBC6} - System32\Tasks\Apple\AppleSoftwareUpdate => C:\Program Files (x86)\Apple Software Update\SoftwareUpdate.exe [2016-02-23] (Apple Inc.)
Task: C:\Windows\Tasks\EPSON WF-2660 Series Update {7A42C501-E959-4055-A7F6-78911F11D381}.job => C:\Windows\system32\spool\DRIVERS\x64\3\E_YTSMAE.EXE�:/EXE:{7A42C501-E959-4055-A7F6-78911F11D381} /F:Update��WORKGROUP\DESKTOP-59CHQV7$�ĊSearches for EPSON software updates, and notifies you when updates are available.If this task is disabled or stopped, your EPSON software will not be automatically kept up to date.Thi
Task: C:\Windows\Tasks\EPSON WF-2660 Series Update {7EA151B1-EAF2-4423-B8EB-50D0B7D5DF45}.job => C:\Windows\system32\spool\DRIVERS\x64\3\E_YTSMAE.EXE�:/EXE:{7EA151B1-EAF2-4423-B8EB-50D0B7D5DF45} /F:Update��WORKGROUP\DESKTOP-59CHQV7$�ĊSearches for EPSON software updates, and notifies you when updates are available.If this task is disabled or stopped, your EPSON software will not be automatically kept up to date.Thi
C:\Users\CRJ\AppData\Local\Temp
RemoveProxy:
CMD: netsh advfirewall reset
CMD: netsh advfirewall set allprofiles state ON
CMD: ipconfig /flushdns
Hosts:
Reboot:
end
*****************
Restore point was successfully created.
Processes closed successfully.
HKU\S-1-5-21-517047234-2264697268-270894284-1001\Software\Microsoft\Windows\CurrentVersion\Run\\BingSvc => value removed successfully
HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{186b6caa-c16c-11e5-b600-806e6f6e6963} => key removed successfully
HKCR\CLSID\{186b6caa-c16c-11e5-b600-806e6f6e6963} => key not found.
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters\\DhcpNameServer => value removed successfully
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{ee5e4c75-c85d-40a3-bd68-be942d47caa5}\\DhcpNameServer => value removed successfully
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{f7f70cc0-e9e3-4107-af44-16e61c7af5d0}\\DhcpNameServer => value removed successfully
HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Google\Chrome\Extensions\fcfenmboojpjinhpgggodefccipikbpd => key removed successfully
HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Google\Chrome\Extensions\lmjegmlicamnimmfhcmpkclmigmmcbeh => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Logon\{30F7F9CC-172A-4F36-A08C-13D4D7755C15} => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{30F7F9CC-172A-4F36-A08C-13D4D7755C15} => key removed successfully
C:\Windows\System32\Tasks\GoogleUpdateTaskMachineCore => moved successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\GoogleUpdateTaskMachineCore => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Plain\{B51668C0-CB6F-4E85-9B47-3625060731EC} => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{B51668C0-CB6F-4E85-9B47-3625060731EC} => key removed successfully
C:\Windows\System32\Tasks\EPSON WF-2660 Series Update {7A42C501-E959-4055-A7F6-78911F11D381} => moved successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\EPSON WF-2660 Series Update {7A42C501-E959-4055-A7F6-78911F11D381} => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Plain\{B6377F1B-92D9-4EAB-BF75-2A9E7F147880} => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{B6377F1B-92D9-4EAB-BF75-2A9E7F147880} => key removed successfully
C:\Windows\System32\Tasks\GoogleUpdateTaskMachineUA => moved successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\GoogleUpdateTaskMachineUA => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Plain\{D8F55054-7AEF-4343-8B4B-8863A85C9B15} => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{D8F55054-7AEF-4343-8B4B-8863A85C9B15} => key removed successfully
C:\Windows\System32\Tasks\Microsoft\Windows\RemovalTools\MRT_HB => moved successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\Microsoft\Windows\RemovalTools\MRT_HB => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Plain\{F0F421B5-4194-4B5E-9637-35C30E22FBC6} => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{F0F421B5-4194-4B5E-9637-35C30E22FBC6} => key removed successfully
C:\Windows\System32\Tasks\Apple\AppleSoftwareUpdate => moved successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\Apple\AppleSoftwareUpdate => key removed successfully
C:\Windows\Tasks\EPSON WF-2660 Series Update {7A42C501-E959-4055-A7F6-78911F11D381}.job => moved successfully
C:\Windows\Tasks\EPSON WF-2660 Series Update {7EA151B1-EAF2-4423-B8EB-50D0B7D5DF45}.job => moved successfully
C:\Users\CRJ\AppData\Local\Temp => moved successfully
========= RemoveProxy: =========
HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\\DefaultConnectionSettings => value removed successfully
HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\\SavedLegacySettings => value removed successfully
HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\\DefaultConnectionSettings => value removed successfully
HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\\SavedLegacySettings => value removed successfully
========= End of RemoveProxy: =========
========= netsh advfirewall reset =========
Ok.
========= End of CMD: =========
========= netsh advfirewall set allprofiles state ON =========
Ok.
========= End of CMD: =========
========= ipconfig /flushdns =========
Windows IP Configuration
Successfully flushed the DNS Resolver Cache.
========= End of CMD: =========
C:\Windows\System32\Drivers\etc\hosts => moved successfully
Hosts restored successfully.
=========== EmptyTemp: ==========
BITS transfer queue => 32768 B
DOMStore, IE Recovery, AppCache, Feeds Cache, Thumbcache, IconCache => 59747642 B
Java, Flash, Steam htmlcache => 21730101 B
Windows/system/drivers => 578325814 B
Edge => 8668004 B
Chrome => 492476128 B
Firefox => 0 B
Opera => 0 B
Temp, IE cache, history, cookies, recent:
Default => 0 B
Users => 0 B
ProgramData => 0 B
Public => 0 B
systemprofile => 128 B
systemprofile32 => 128 B
LocalService => 61440 B
NetworkService => 983408 B
CRJ => 14788726 B
Connor => 212133244 B
RecycleBin => 3191617918 B
EmptyTemp: => 4.3 GB temporary data Removed.
================================
The system needed a reboot.
==== End of Fixlog 09:23:42 ====
Ran by CRJ (18-02-2017 09:23:20) Run:1
Running from C:\Users\CRJ\Desktop
Loaded Profiles: CRJ (Available Profiles: CRJ & Connor)
Boot Mode: Normal
==============================================
fixlist content:
*****************
Start
CreateRestorePoint:
Closeprocesses:
Emptytemp:
HKU\S-1-5-21-517047234-2264697268-270894284-1001\...\Run: [BingSvc] => C:\Users\CRJ\AppData\Local\Microsoft\BingSvc\BingSvc.exe [144008 2015-11-05] (© 2015 Microsoft Corporation)
HKU\S-1-5-21-517047234-2264697268-270894284-1001\...\MountPoints2: {186b6caa-c16c-11e5-b600-806e6f6e6963} - "D:\Run.exe"
Tcpip\Parameters: [DhcpNameServer] 75.75.76.76 75.75.75.75
Tcpip\..\Interfaces\{ee5e4c75-c85d-40a3-bd68-be942d47caa5}: [DhcpNameServer] 75.75.76.76 75.75.75.75
Tcpip\..\Interfaces\{f7f70cc0-e9e3-4107-af44-16e61c7af5d0}: [DhcpNameServer] 75.75.76.76 75.75.75.75
CHR HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Google\Chrome\Extensions\...\Chrome\Extension: [fcfenmboojpjinhpgggodefccipikbpd] - hxxps://clients2.google.com/service/update2/crx
CHR HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Google\Chrome\Extensions\...\Chrome\Extension: [lmjegmlicamnimmfhcmpkclmigmmcbeh] - hxxps://clients2.google.com/service/update2/crx
Task: {30F7F9CC-172A-4F36-A08C-13D4D7755C15} - System32\Tasks\GoogleUpdateTaskMachineCore => C:\Program Files (x86)\Google\Update\GoogleUpdate.exe [2016-01-23] (Google Inc.)
Task: {B51668C0-CB6F-4E85-9B47-3625060731EC} - System32\Tasks\EPSON WF-2660 Series Update {7A42C501-E959-4055-A7F6-78911F11D381} => C:\Windows\system32\spool\DRIVERS\x64\3\E_YTSMAE.EXE [2013-11-22] (SEIKO EPSON CORPORATION)
Task: {B6377F1B-92D9-4EAB-BF75-2A9E7F147880} - System32\Tasks\GoogleUpdateTaskMachineUA => C:\Program Files (x86)\Google\Update\GoogleUpdate.exe [2016-01-23] (Google Inc.)
Task: {D8F55054-7AEF-4343-8B4B-8863A85C9B15} - System32\Tasks\Microsoft\Windows\RemovalTools\MRT_HB => C:\Windows\system32\MRT.exe [2017-01-11] (Microsoft Corporation)
Task: {F0F421B5-4194-4B5E-9637-35C30E22FBC6} - System32\Tasks\Apple\AppleSoftwareUpdate => C:\Program Files (x86)\Apple Software Update\SoftwareUpdate.exe [2016-02-23] (Apple Inc.)
Task: C:\Windows\Tasks\EPSON WF-2660 Series Update {7A42C501-E959-4055-A7F6-78911F11D381}.job => C:\Windows\system32\spool\DRIVERS\x64\3\E_YTSMAE.EXE�:/EXE:{7A42C501-E959-4055-A7F6-78911F11D381} /F:Update��WORKGROUP\DESKTOP-59CHQV7$�ĊSearches for EPSON software updates, and notifies you when updates are available.If this task is disabled or stopped, your EPSON software will not be automatically kept up to date.Thi
Task: C:\Windows\Tasks\EPSON WF-2660 Series Update {7EA151B1-EAF2-4423-B8EB-50D0B7D5DF45}.job => C:\Windows\system32\spool\DRIVERS\x64\3\E_YTSMAE.EXE�:/EXE:{7EA151B1-EAF2-4423-B8EB-50D0B7D5DF45} /F:Update��WORKGROUP\DESKTOP-59CHQV7$�ĊSearches for EPSON software updates, and notifies you when updates are available.If this task is disabled or stopped, your EPSON software will not be automatically kept up to date.Thi
C:\Users\CRJ\AppData\Local\Temp
RemoveProxy:
CMD: netsh advfirewall reset
CMD: netsh advfirewall set allprofiles state ON
CMD: ipconfig /flushdns
Hosts:
Reboot:
end
*****************
Restore point was successfully created.
Processes closed successfully.
HKU\S-1-5-21-517047234-2264697268-270894284-1001\Software\Microsoft\Windows\CurrentVersion\Run\\BingSvc => value removed successfully
HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{186b6caa-c16c-11e5-b600-806e6f6e6963} => key removed successfully
HKCR\CLSID\{186b6caa-c16c-11e5-b600-806e6f6e6963} => key not found.
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters\\DhcpNameServer => value removed successfully
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{ee5e4c75-c85d-40a3-bd68-be942d47caa5}\\DhcpNameServer => value removed successfully
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{f7f70cc0-e9e3-4107-af44-16e61c7af5d0}\\DhcpNameServer => value removed successfully
HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Google\Chrome\Extensions\fcfenmboojpjinhpgggodefccipikbpd => key removed successfully
HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Google\Chrome\Extensions\lmjegmlicamnimmfhcmpkclmigmmcbeh => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Logon\{30F7F9CC-172A-4F36-A08C-13D4D7755C15} => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{30F7F9CC-172A-4F36-A08C-13D4D7755C15} => key removed successfully
C:\Windows\System32\Tasks\GoogleUpdateTaskMachineCore => moved successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\GoogleUpdateTaskMachineCore => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Plain\{B51668C0-CB6F-4E85-9B47-3625060731EC} => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{B51668C0-CB6F-4E85-9B47-3625060731EC} => key removed successfully
C:\Windows\System32\Tasks\EPSON WF-2660 Series Update {7A42C501-E959-4055-A7F6-78911F11D381} => moved successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\EPSON WF-2660 Series Update {7A42C501-E959-4055-A7F6-78911F11D381} => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Plain\{B6377F1B-92D9-4EAB-BF75-2A9E7F147880} => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{B6377F1B-92D9-4EAB-BF75-2A9E7F147880} => key removed successfully
C:\Windows\System32\Tasks\GoogleUpdateTaskMachineUA => moved successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\GoogleUpdateTaskMachineUA => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Plain\{D8F55054-7AEF-4343-8B4B-8863A85C9B15} => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{D8F55054-7AEF-4343-8B4B-8863A85C9B15} => key removed successfully
C:\Windows\System32\Tasks\Microsoft\Windows\RemovalTools\MRT_HB => moved successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\Microsoft\Windows\RemovalTools\MRT_HB => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Plain\{F0F421B5-4194-4B5E-9637-35C30E22FBC6} => key removed successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{F0F421B5-4194-4B5E-9637-35C30E22FBC6} => key removed successfully
C:\Windows\System32\Tasks\Apple\AppleSoftwareUpdate => moved successfully
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\Apple\AppleSoftwareUpdate => key removed successfully
C:\Windows\Tasks\EPSON WF-2660 Series Update {7A42C501-E959-4055-A7F6-78911F11D381}.job => moved successfully
C:\Windows\Tasks\EPSON WF-2660 Series Update {7EA151B1-EAF2-4423-B8EB-50D0B7D5DF45}.job => moved successfully
C:\Users\CRJ\AppData\Local\Temp => moved successfully
========= RemoveProxy: =========
HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\\DefaultConnectionSettings => value removed successfully
HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\\SavedLegacySettings => value removed successfully
HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\\DefaultConnectionSettings => value removed successfully
HKU\S-1-5-21-517047234-2264697268-270894284-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\\SavedLegacySettings => value removed successfully
========= End of RemoveProxy: =========
========= netsh advfirewall reset =========
Ok.
========= End of CMD: =========
========= netsh advfirewall set allprofiles state ON =========
Ok.
========= End of CMD: =========
========= ipconfig /flushdns =========
Windows IP Configuration
Successfully flushed the DNS Resolver Cache.
========= End of CMD: =========
C:\Windows\System32\Drivers\etc\hosts => moved successfully
Hosts restored successfully.
=========== EmptyTemp: ==========
BITS transfer queue => 32768 B
DOMStore, IE Recovery, AppCache, Feeds Cache, Thumbcache, IconCache => 59747642 B
Java, Flash, Steam htmlcache => 21730101 B
Windows/system/drivers => 578325814 B
Edge => 8668004 B
Chrome => 492476128 B
Firefox => 0 B
Opera => 0 B
Temp, IE cache, history, cookies, recent:
Default => 0 B
Users => 0 B
ProgramData => 0 B
Public => 0 B
systemprofile => 128 B
systemprofile32 => 128 B
LocalService => 61440 B
NetworkService => 983408 B
CRJ => 14788726 B
Connor => 212133244 B
RecycleBin => 3191617918 B
EmptyTemp: => 4.3 GB temporary data Removed.
================================
The system needed a reboot.
==== End of Fixlog 09:23:42 ====
~ ZHPCleaner v2017.2.16.28 by Nicolas Coolman (2017/02/16)
~ Run by CRJ (Administrator) (18/02/2017 09:47:57)
~ Web: https://www.nicolascoolman.com
~ Blog: https://nicolascoolman.eu/
~ Facebook : https://www.facebook.com/nicolascoolman1
~ State version : Version OK
~ Type : Repair
~ Report : C:\Users\CRJ\Desktop\ZHPCleaner.txt
~ Quarantine : C:\Users\CRJ\AppData\Roaming\ZHP\ZHPCleaner_Quarantine.txt
~ UAC : Activate
~ Boot Mode : Normal (Normal boot)
Windows 10 Home, 64-bit (Build 10586)
---\\ Services (1)
CLOSED : EasyTuneEngineService =>Heuristic.Pirrit
---\\ Browser internet (0)
~ No malicious or unnecessary items found.
---\\ Hosts file (1)
~ The hosts file is legitimate (1)
---\\ Scheduled automatic tasks. (0)
~ No malicious or unnecessary items found.
---\\ Explorer ( File, Folder) (30)
MOVED file: C:\Windows\Installer\wix{2E4AF2A6-50EA-4260-9BA4-5E582D11879A}.SchedServiceConfig.rmi =>.Superfluous.Empty
MOVED file: C:\Windows\Installer\wix{3540181E-340A-4E7A-B409-31663472B2F7}.SchedServiceConfig.rmi =>.Superfluous.Empty
MOVED file: C:\Windows\Installer\wix{55BB2110-FB43-49B3-93F4-945A0CFB0A6C}.SchedServiceConfig.rmi =>.Superfluous.Empty
MOVED file: C:\Windows\Installer\wix{CDB60A91-DA13-41AA-A827-7967BEC75AF8}.SchedServiceConfig.rmi =>.Superfluous.Empty
MOVED file: C:\Windows\Installer\wix{D4D86CB2-2370-4691-8272-3869EDED6C64}.SchedServiceConfig.rmi =>.Superfluous.Empty
MOVED file: C:\Users\CRJ\AppData\Local\Temp\wct880C.tmp =>.Superfluous.Temporary.Various
MOVED file: C:\Users\CRJ\AppData\Local\Temp\wct8F76.tmp =>.Superfluous.Temporary.Various
MOVED folder^: C:\Program Files (x86)\GIGABYTE\EasyTuneEngineService =>Heuristic.Pirrit
MOVED folder: C:\Program Files (x86)\QuickTime =>Riskware.QuickTime
MOVED folder: C:\Users\CRJ\AppData\Local\Google\Chrome\User Data\Default\File System\008 =>PUP.Optional.DomaIQ
MOVED folder: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\QuickTime =>Riskware.QuickTime
MOVED folder: C:\Windows\Installer\MSI1EDB.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI1F69.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI1FB8.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI28F7.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI307A.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI30E9.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI3138.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI7C30.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI7CEC.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI7DB9.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI8346.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI83A5.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI8413.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI980A.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI9916.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSICFD6.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSID1BE.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSID733.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSIDE0B.tmp- =>.Superfluous.Empty
---\\ Registry ( Key, Value, Data) (5)
DELETED key*: HKLM\SYSTEM\CurrentControlSet\Services\EasyTuneEngineService [C:\Program Files (x86)\GIGABYTE\EasyTuneEngineService\EasyTuneEngineService.exe] =>Heuristic.Pirrit
DELETED key*: HKLM\SYSTEM\CurrentControlSet\Services\OcButtonService [C:\Program Files (x86)\GIGABYTE\EasyTuneEngineService\OcButtonService.exe (Not File)] =>Heuristic.Pirrit
DELETED key*: [X64] HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\018DB0496FC46614CBED2103F75B7262 [C:\?Program Files (x86)\GIGABYTE\EasyTuneEngineService\acpimof_ocpanel.dll (Not File)] =>Heuristic.Pirrit
DELETED key*: [X64] HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\0E5B51D5DDC32D34390DD1AF91EF7BA2 [C:\Program Files (x86)\GIGABYTE\EasyTuneEngineService\Languages\ARA\ (Not File)] =>Heuristic.Pirrit
DELETED key*: [X64] HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\0E779259750044C565F4587810BED609 [C:\?Program Files (x86)\GIGABYTE\EasyTuneEngineService\ICCProxy.exe (Not File)] =>Heuristic.Pirrit
---\\ Summary of the elements found (5)
https://nicolascoolman.eu/2017/01/27/repaquetage-et-infection/ =>Heuristic.Pirrit
https://nicolascoolman.eu/2017/01/20/logiciels-superflus/ =>.Superfluous.Empty
https://nicolascoolman.eu/2017/01/20/logiciels-superflus/ =>.Superfluous.Temporary.Various
https://nicolascoolman.eu/2017/01/15/riskware-quicktime/ =>Riskware.QuickTime
https://www.nicolascoolman.com/fr/adware-domaiq/ =>PUP.Optional.DomaIQ
---\\ Other deletions. (20)
~ Registry Keys Tracing deleted (20)
~ Remove the old reports ZHPCleaner. (0)
---\\ Result of repair
~ Repair carried out successfully
~ Browser not found (Mozilla Firefox)
~ Browser not found (Opera Software)
~ The system has been restarted.
---\\ Statistics
~ Items scanned : 315
~ Items found : 0
~ Items cancelled : 0
~ Items repaired : 37
~ End of clean in 00h00mn15s
~====================
ZHPCleaner-[R]-18022017-09_48_12.txt
ZHPCleaner--18022017-09_43_57.txt
~ Run by CRJ (Administrator) (18/02/2017 09:47:57)
~ Web: https://www.nicolascoolman.com
~ Blog: https://nicolascoolman.eu/
~ Facebook : https://www.facebook.com/nicolascoolman1
~ State version : Version OK
~ Type : Repair
~ Report : C:\Users\CRJ\Desktop\ZHPCleaner.txt
~ Quarantine : C:\Users\CRJ\AppData\Roaming\ZHP\ZHPCleaner_Quarantine.txt
~ UAC : Activate
~ Boot Mode : Normal (Normal boot)
Windows 10 Home, 64-bit (Build 10586)
---\\ Services (1)
CLOSED : EasyTuneEngineService =>Heuristic.Pirrit
---\\ Browser internet (0)
~ No malicious or unnecessary items found.
---\\ Hosts file (1)
~ The hosts file is legitimate (1)
---\\ Scheduled automatic tasks. (0)
~ No malicious or unnecessary items found.
---\\ Explorer ( File, Folder) (30)
MOVED file: C:\Windows\Installer\wix{2E4AF2A6-50EA-4260-9BA4-5E582D11879A}.SchedServiceConfig.rmi =>.Superfluous.Empty
MOVED file: C:\Windows\Installer\wix{3540181E-340A-4E7A-B409-31663472B2F7}.SchedServiceConfig.rmi =>.Superfluous.Empty
MOVED file: C:\Windows\Installer\wix{55BB2110-FB43-49B3-93F4-945A0CFB0A6C}.SchedServiceConfig.rmi =>.Superfluous.Empty
MOVED file: C:\Windows\Installer\wix{CDB60A91-DA13-41AA-A827-7967BEC75AF8}.SchedServiceConfig.rmi =>.Superfluous.Empty
MOVED file: C:\Windows\Installer\wix{D4D86CB2-2370-4691-8272-3869EDED6C64}.SchedServiceConfig.rmi =>.Superfluous.Empty
MOVED file: C:\Users\CRJ\AppData\Local\Temp\wct880C.tmp =>.Superfluous.Temporary.Various
MOVED file: C:\Users\CRJ\AppData\Local\Temp\wct8F76.tmp =>.Superfluous.Temporary.Various
MOVED folder^: C:\Program Files (x86)\GIGABYTE\EasyTuneEngineService =>Heuristic.Pirrit
MOVED folder: C:\Program Files (x86)\QuickTime =>Riskware.QuickTime
MOVED folder: C:\Users\CRJ\AppData\Local\Google\Chrome\User Data\Default\File System\008 =>PUP.Optional.DomaIQ
MOVED folder: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\QuickTime =>Riskware.QuickTime
MOVED folder: C:\Windows\Installer\MSI1EDB.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI1F69.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI1FB8.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI28F7.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI307A.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI30E9.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI3138.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI7C30.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI7CEC.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI7DB9.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI8346.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI83A5.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI8413.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI980A.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSI9916.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSICFD6.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSID1BE.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSID733.tmp- =>.Superfluous.Empty
MOVED folder: C:\Windows\Installer\MSIDE0B.tmp- =>.Superfluous.Empty
---\\ Registry ( Key, Value, Data) (5)
DELETED key*: HKLM\SYSTEM\CurrentControlSet\Services\EasyTuneEngineService [C:\Program Files (x86)\GIGABYTE\EasyTuneEngineService\EasyTuneEngineService.exe] =>Heuristic.Pirrit
DELETED key*: HKLM\SYSTEM\CurrentControlSet\Services\OcButtonService [C:\Program Files (x86)\GIGABYTE\EasyTuneEngineService\OcButtonService.exe (Not File)] =>Heuristic.Pirrit
DELETED key*: [X64] HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\018DB0496FC46614CBED2103F75B7262 [C:\?Program Files (x86)\GIGABYTE\EasyTuneEngineService\acpimof_ocpanel.dll (Not File)] =>Heuristic.Pirrit
DELETED key*: [X64] HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\0E5B51D5DDC32D34390DD1AF91EF7BA2 [C:\Program Files (x86)\GIGABYTE\EasyTuneEngineService\Languages\ARA\ (Not File)] =>Heuristic.Pirrit
DELETED key*: [X64] HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\0E779259750044C565F4587810BED609 [C:\?Program Files (x86)\GIGABYTE\EasyTuneEngineService\ICCProxy.exe (Not File)] =>Heuristic.Pirrit
---\\ Summary of the elements found (5)
https://nicolascoolman.eu/2017/01/27/repaquetage-et-infection/ =>Heuristic.Pirrit
https://nicolascoolman.eu/2017/01/20/logiciels-superflus/ =>.Superfluous.Empty
https://nicolascoolman.eu/2017/01/20/logiciels-superflus/ =>.Superfluous.Temporary.Various
https://nicolascoolman.eu/2017/01/15/riskware-quicktime/ =>Riskware.QuickTime
https://www.nicolascoolman.com/fr/adware-domaiq/ =>PUP.Optional.DomaIQ
---\\ Other deletions. (20)
~ Registry Keys Tracing deleted (20)
~ Remove the old reports ZHPCleaner. (0)
---\\ Result of repair
~ Repair carried out successfully
~ Browser not found (Mozilla Firefox)
~ Browser not found (Opera Software)
~ The system has been restarted.
---\\ Statistics
~ Items scanned : 315
~ Items found : 0
~ Items cancelled : 0
~ Items repaired : 37
~ End of clean in 00h00mn15s
~====================
ZHPCleaner-[R]-18022017-09_48_12.txt
ZHPCleaner-
Attachments
Last edited by a moderator:
Had to change the file name to the correct one. lol
Sorry about that typo...
Recommendations on what to maintain going forward would be great.
You can manually delete the C:\Windows\system32\{A6D608F0-0BDE-491A-97AE-5C4B05D86E01}.bat file, through windows explorer.
Glad to have helped!! Please tell a friend ...... or two about us.
Optimize your internet connection.
Click here for instructions.
suggest the following in place of adblock.
Alternate DNS Server. Ad Blocking DNS.
Ublock Origin.
Anti Ad Block Killer.
Also, keep your browsing private with these tools:
Self Destructing Cookies.
Self Destructing Cookies Chrome.
Some items to keep you safe on the internet.
VooDoo Shield. control of what is running on your machine
Qualys BrowserCheck To update plugins.
Web Of Trust To Avoid Shady Websites.
Unchecky To Avoid Bundled Software.
Privazer To Clean up your mahcine.
Now Lets Clean up the tools we used and remove old restore points.
Download DelFix by "Xplode" to your Desktop.
Right Click the tool and Run as Admin ( Xp Users Double Click)
Put a check mark next the items below:
Remove disinfection tools
Create registry backup
Purge System Restore
Now click on "Run" button.
allow the program to complete its work.
all the tools we used will be removed.
Tool will create and open a log report (DelFix.txt)
Note: The report can be located at the following location C:\DelFix.txt
- Status
- Not open for further replies.